Secure Global Restuarant Network System Design and Implementation
Scenario Description: Secure Hotel/Restuarant Network:
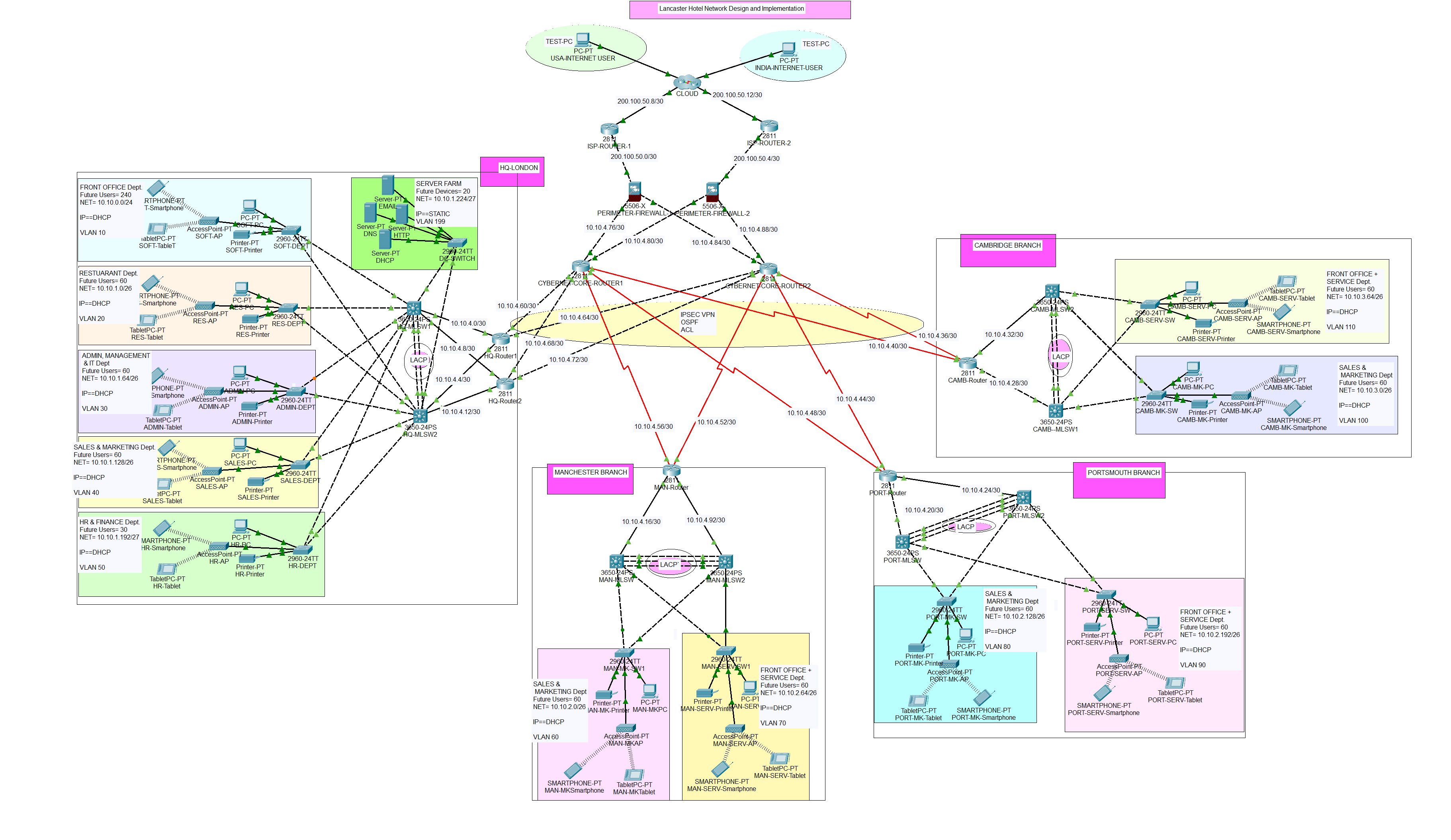
This network design represents the Lancaster Hotel Network system in which the company is comprised of the headquarters located in London and the other three branches located in Manchester, Portsmouth, and Cambridge. The London site is expected to have 6 departments that include Front Office and Service (100 employees), Restaurant (30 employees), Admin/Management/IT (30 employees), Sales and Marketing (30 employees), and finally, HR and Finance (15 employees) departments. In every branch site, there are two departments each and they include Sales and Marketing (15 employees), and Front Office and Service (15 employees). The employees in each department are expected to double in the future and therefore this should be taken into consideration during the design and implementation.
The ICT and other departments at the headquarters are expected to provide support for all the branches remotely and therefore SSH and site-to-site IPsec VPN should be used to realize secure communication between the HQ and the branches. The network is expected to be more secure, of high performance, and redundant to eliminate a single point of failure and for load-balancing.
- Creating a network topology using Cisco Packet Tracer.
- Hierarchical Network Design.
- Connecting Networking devices with Correct cabling.
- Configuring Basic device settings.
- Creating VLANs and assigning ports VLAN numbers.
- Creating both data and voice VLANs and assigning ports VLAN numbers.
- Subnetting and IP Addressing.
- Configuring Inter-VLAN Routing both on the Switches (SVI) and Routers (router-on-a-stick).
- Configuring Dedicated DHCP Server device for Data to provide dynamic IP allocation.
- Configuring Routers as DHCP server for Voice to provide IP Phones dynamic IP allocation.
- Configuring link aggregation or EtherChannel using LACP
- Configuring SSH for secure Remote access.
- Configuring OSPF as the routing protocol.
- Configuring Standard ACL for VTY interfaces to restrict remote Access using SSH.
- Configuring Port Address Translation or PAT for NAT.
- Configuring Standard ACL for PAT.
- Configuring VoIP or Telephony service configuration in all routers.
- Configuring site-to-site IPsec VPN on the gateway routers.
- Configuring Standard ACL for site-to-site IPsec VPN.
- Configuration of Cisco ASA firewall to filter inbound and outbound traffic.
- Configuring security levels and zones on a Cisco ASA firewall.
- Configuring default static route on a Cisco ASA firewall.
- Configuring network objects on a Cisco ASA firewall.
- Configuring inspection policy on a Cisco ASA firewall.
- Configuring ISP routers.
- Testing and verifying Network Communication.
The network topology below satisfy the user requirements above and everything is verified, tested and working fine.