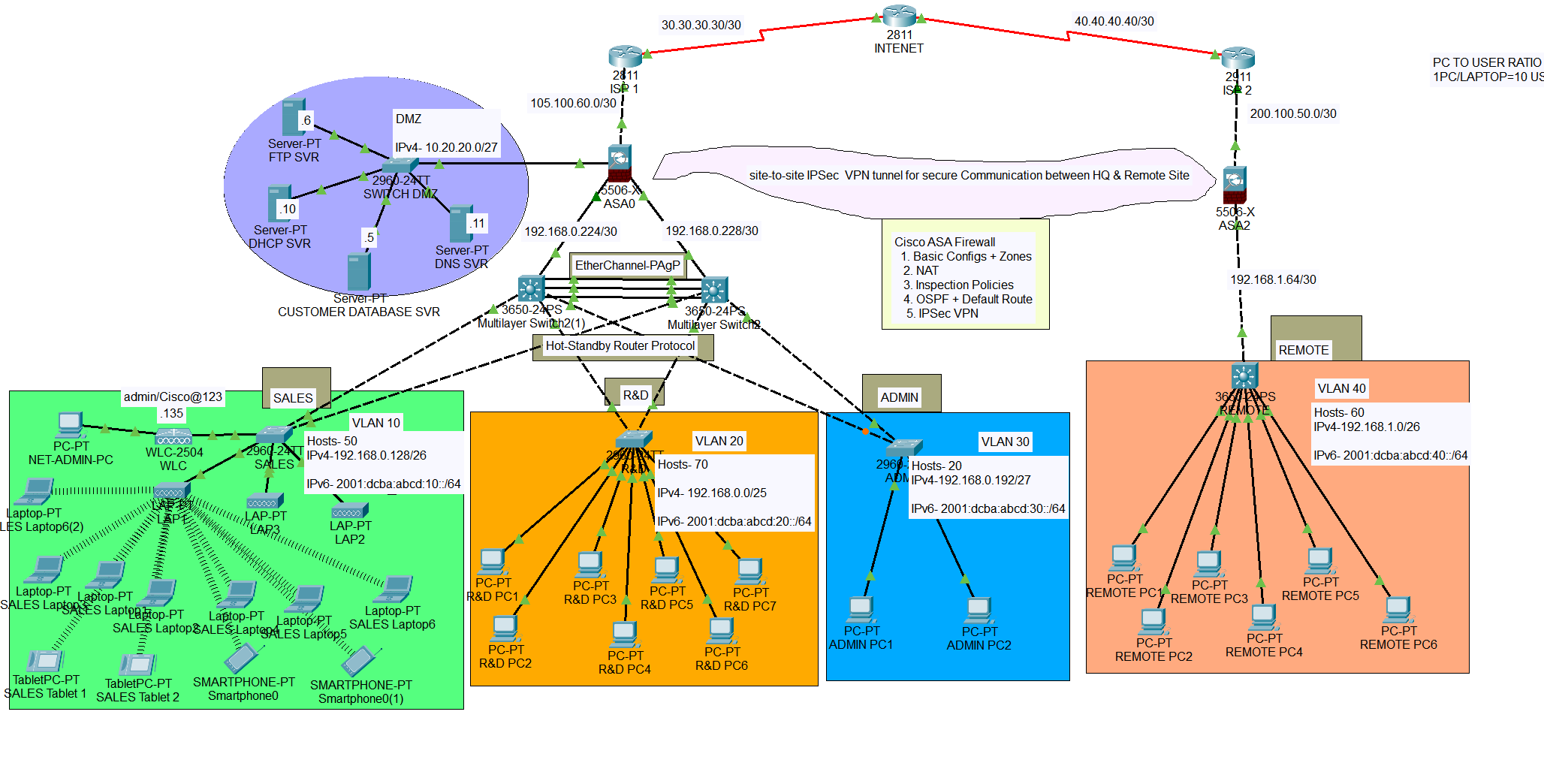
Secure Digital Tech Company Network System Design and Implementation
Scenario Description: Secure Digital Tech Company Network:
Digitech Technologies is a medium-sized tech firm based in Nairobi, Kenya. Established in 2020, it specialises in developing innovative software solutions for a diverse clientele, ranging from small businesses to large corporations in both private and public sector. The firm boasts of a dynamic workforce of 200 employees, distributed across four key departments: Sales, R&D, Administration, and Remote Workers.
The Sales department, consisting of 50 staff members, frequently communicates with clients and requires continuous access to customer databases. The R&D team, with 70 dedicated researchers and developers, often collaborates on cutting-edge projects, necessitating a high level of data security and speed. The Administration department, a team of 20, handles sensitive employee data, financial records, and company-wide communications. Lastly, the Remote Workers, accounting for the remaining 60 employees, operate from various locations worldwide, needing secure and efficient remote access solutions.
Each department has unique security and network needs, reflecting their distinct roles within the organisation. Your task is to design and implement a secure network that ensures data integrity, availability, confidentiality, and optimal performance.
Your report should consider these aspects:
• Design Decisions: Your design decisions should cater to the specific needs of Digitech Technologies and adhere to best practices in network design and security.
• Documentation: Every claim or decision in your report must be substantiated by evidence, be it in the form of screenshots, diagrams, or other pertinent documentation.
• Practical Implementation: Where feasible, bring your designs to life in a virtual environment to verify their functionality.
• Report Structure: Your report should exhibit a clear structure, encompassing an introduction, methodology, design decisions, justifications, and conclusion.
- Network Topology Design • Create a logical design of the entire network.
- IP Addressing and VLAN Configuration • Allocate IP addresses for each device and segment.
- Routing, Access Control, and Network Segmentation • Define routing paths for efficient data flow.
- Wireless Network Design & VPN Configuration • Set up a secure wireless network for the Sales department.
- Report & Justification • Compile your decisions, configurations, and screenshots into a report.
• Consider placement of routers, switches, firewalls, and other relevant devices.
• Document with a clear diagram.
• Implement VLANs for each department.
• Document your design choices and configurations.
• Verify the connectivity post-configuration to ensure network integrity.
• Implement Access Control Lists (ACLs) for each department.
• Document your decisions and configurations.
• Verify the connectivity post-configuration to ensure all routing paths and access controls are correctly implemented.
• Configure a VPN for the Remote Workers.
• Document security measures, configurations, and justifications.
• Verify that the implemented security measures and configurations achieve the intended security requirements.
• Ensure clarity, structure, and professionalism in your report.
The network topology below satisfy the user requirements above and everything is verified, tested and working fine.