Secure Financial Services Limited Network System Design and Implementation
Scenario Description: Secure Financial Services Network:
Company Overview:
NewHaven Financial Services Ltd (JFSL) is a reputable financial services provider based in New Haven, United States, operating within an eleven-story building. The company's main headquarters are located on the seventh and eighth floors, where each floor accommodates multiple departments. These include Human Resources (HR), Customer Service (CS), Marketing (MK), Legal Management (LM), and Information Technology (IT).
On the seventh floor, the HR, CS, and MK departments each comprise a minimum of 300 user devices, 50 IP phones, and one WIFI access point. Similarly, on the eighth floor, the LM and IT departments consist of at least 350 user devices, 40 IP phones, and one WIFI access point.
Customer Requirements and Goals:
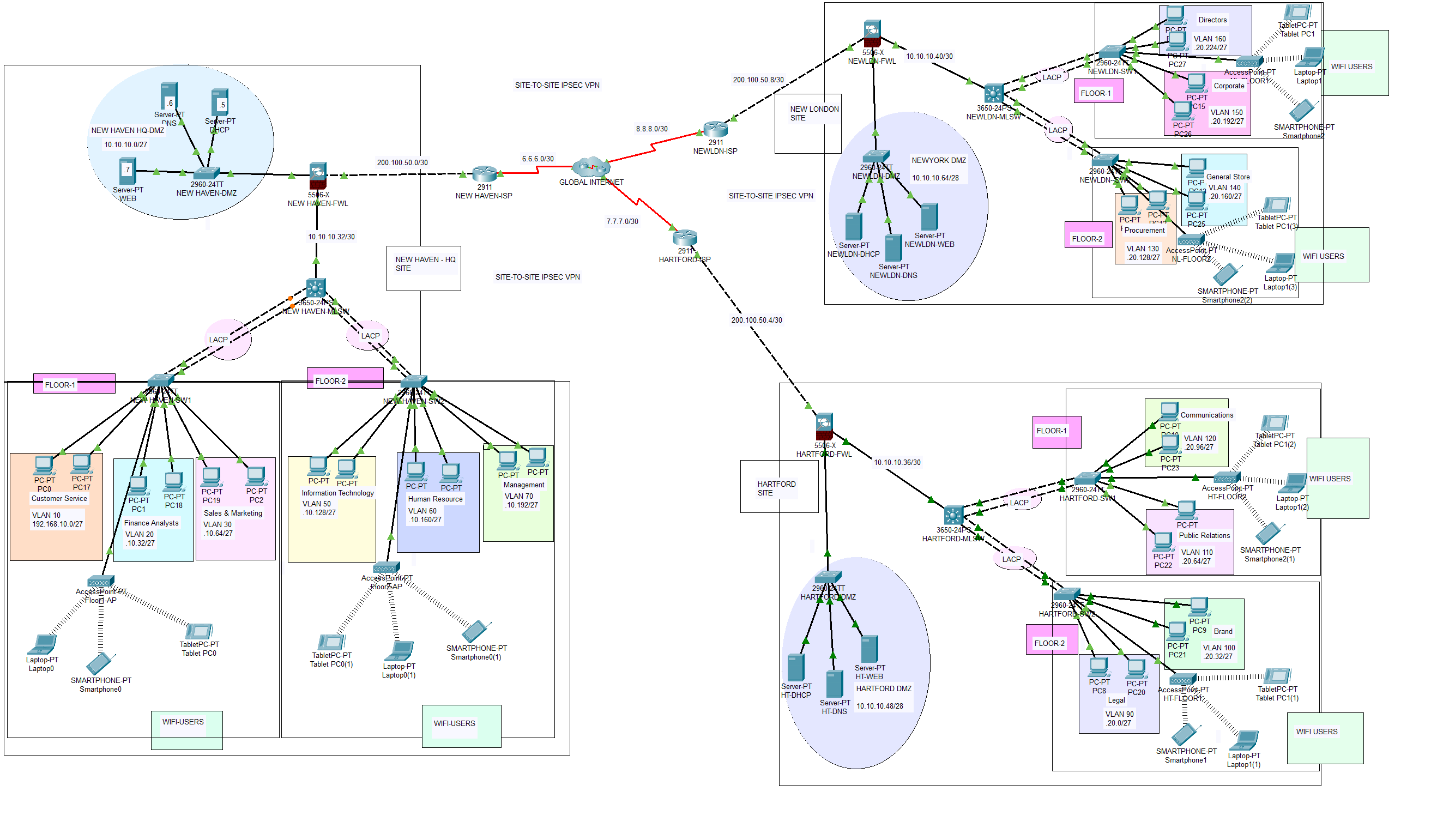
The current network infrastructure management, handled by Infinitive IT Systems, will transition to in-house control, following a decision by senior management at NewHaven Financial Services Ltd (NFSL). This transition encompasses ownership of the Local Area Network (LAN), Wide Area Network (WAN), and an external server-side location, prioritizing secure communication between the headquarters network and the external site. The server-side location will host critical servers for functions such as DHCP, DNS, WEB, and EMAIL services.
To ensure reliability and redundancy in internet connectivity, NFSL plans to subscribe to two ISPs, Safaricom and JTL ISPs. This setup will provide load-balancing capabilities and redundancy in case of internet service disruptions. Additionally, NFSL has procured networking equipment, including two Cisco Catalyst 2911 routers (one for headquarters and the other for the server-side), a Catalyst 2811 router for headquarters VoIP services, two multilayer switches for headquarters, and six access switches for departmental use.
In alignment with stringent security requirements, each of the five departments at NFSL will operate on a separate network segment within the same LAN. Notably, none of the critical servers will reside within the LAN but will instead be hosted externally and accessed via WAN connections. Access to the external site will be governed by a comprehensive network security policy, enforced through Access Control Lists (ACLs), regulating user access and ensuring data security.
- Design an Enterprise Network including LAN, WAN, Wireless, and Cloud components
- Detailed network design and analysis are required for a complete project evaluation
- You work as groups of 5 people, and you will submit a major report at the end of your project, and do a presentation, demonstration, and an oral Q/A session.
- Top-down design approach should be used, start from Applications down to Network, Data Link and Media layers:
- Explain in detail your choice of applications, routing protocols, switching mechanism, and media used
- Explain in detail your addressing and naming choices
- Follow the life cycle of a network design process including: - Phase 1 – Identifying Customer Needs/Goals
- WAN should have three hierarchical layers: Core, Distribution, and Access networks
- LAN should be established in each building by collecting traffic from each floor (wiring closet), passing down to the server room
- Each floor should have a gateway to the exit point of the building, and each building has gateway to the public network
- Physical and logical topologies of both LAN and WAN
- Service Provider (ISP) and enterprise parts of the network
- Technologies and devices used and traffic analysis
- Use of Cloud, private or public (To Cloud or not To Cloud)
- WAN: • Several locations across the nation
- LAN: • Each campus should have several buildings
- Storage Area • LAN security measures: AAA servers, firewalls, Authentication, Encryption
- Wireless: • You could include one or more wireless technology to your project in order to improve your enterprise network accessibility. Typical wireless technologies in an enterprise are WiFi, WiMAX, Cellular systems (LTE), Bluetooth, ZigBee, Wireless Local Loop (WLL), etc.
- Cloud Computing: • You could consider to use a cloud system (either public or private) to enhance your enterprise network capability. Cloud environment could be deployed for your network and cloud services could be used for both your enterprise employee and/or for your customers. Based on your technical evaluation decide whether to go with the cloud or not, and if you decide to use cloud, which one do you prefer: private or public, and Why?
- Phase 2 – Logical Network Design
- Phase 3 – Physical Network Design
- Phase 4 – Testing/Optimizing/Documenting
Your Enterprise should include:
• At least 1-2 major campus networks
• At least 1-2 small branch office networks • At least one remote branch office
• At least one international branch office
• Several employees that work from home
• Use at least two ISPs for redundancy, load balancing, and backup
• Use of routing protocols - OSPF or EIGRP
• Use of switching technologies, Ethernet (10/100/1000 Mbps), VLANs, Frame Relay
• WAN security measures: VLANS, Access lists on the routers, routing and switching security measure
• Each building should have several floors
• Required Servers on each site and for the entire enterprise: Mail, Web, File, Database, Application, DNS, DHCP,
• WAN security, VPN, Encryption,
• DMZ security: Proxy, Firewall servers. Mail and Web servers should be here
• Use of Cloud environment, public or private
The network topology below satisfy the user requirements above and everything is verified, tested and working fine.